What is NETCONF Protocol?
NETCONF Protocol also called "Network Configuration Protocol" is a network management protocol developed and standardized by the IETF (Internet Engineering Task Force). NETCONF Protocol facilitates the management, configuration, and operation of network devices such as routers, switches, and firewalls. NETCONF Protocol utilizes XML for data encoding and leverages a client-server model to provide mechanisms for installing, manipulating, and deleting the configuration of network devices.
Importance of NETCONF Protocol in Network Management
The importance of NETCONF protocol in network management lies in its ability to provide a standardized and robust framework for network configuration and management. It enhances the automation of network tasks, reduces the risk of configuration errors, and supports the dynamic nature of modern networks. NETCONF protocol's capabilities for transaction management and configuration validation ensure that network changes are applied consistently and reliably.
As organizations increasingly demand real-time insights, ultra-low latency, and resilient distributed systems, Edge Computing is becoming mission-critical. At the same time, technologies like NETCONF are being integrated into Edge environments as a standard management and control layer.
To help professionals move confidently from concepts to execution, our course “Edge Computing Essentials: Concepts to Real-World Use Cases” provides a structured, hands-on learning path covering core principles, architecture, platforms, and enabling technologies—directly mapped to real-world industrial use cases.
If you’re looking to build in-demand skills and accelerate your career in Edge Computing, this is the right place to start.
Key NETCONF Protocol Features
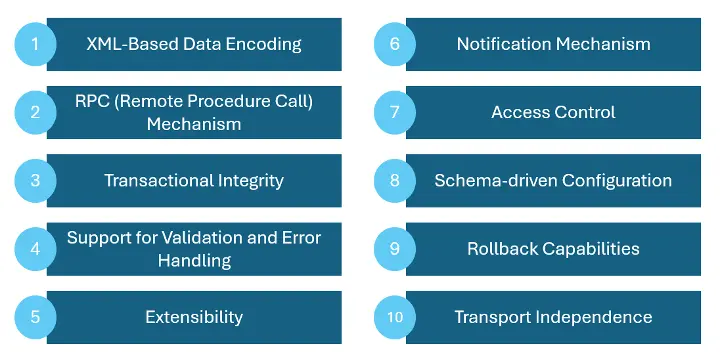
Here are some key NETCONF Protocol Features:
- XML-Based Data Encoding - Uses XML for encoding configuration data, allowing for structured and hierarchical data representation.
- RPC (Remote Procedure Call) Mechanism - Operates over a simple RPC-based mechanism for structured communication.
- Configuration Datastores - Defines multiple datastores (running, startup, candidate) for managing configurations.
- Transactional Integrity - Changes to the network configuration are applied as a single atomic transaction, ensuring consistency and reliability.
- Support for Validation and Error Handling - Includes mechanisms for validating changes and comprehensive error handling.
- Extensibility - NETCONF can be extended with new capabilities and features without disrupting existing functionality.
- Notification Mechanism - Supports asynchronous notifications for significant events.
- Access Control - Integrates with access control mechanisms, including SSH for secure communication.
- Schema-driven Configuration - Utilizes YANG to define the structure of configuration and state data.
- Rollback Capabilities - Ability to revert to a previous configuration state if an error occurs.
- Transport Independence - Operates over various transport protocols such as SSH, BEEP, and TLS.
NETCONF Protocol vs SNMP
Both NETCONF and SNMP (Simple Network Management Protocol) are used for network management, though they have distinct differences:
- Data Representation: NETCONF uses XML, providing a more human-readable and structured data format compared to SNMP’s ASN.1 format.
- Operations: NETCONF supports a richer set of operations for configuration management, whereas SNMP is primarily used for monitoring and simple configuration tasks.
- Security: NETCONF typically runs over SSH or TLS, providing robust security features. SNMPv3 includes security features, but older versions lack strong security mechanisms.
- Capabilities: NETCONF supports more complex configuration tasks and transaction management, making it more suitable for modern, dynamic networks.
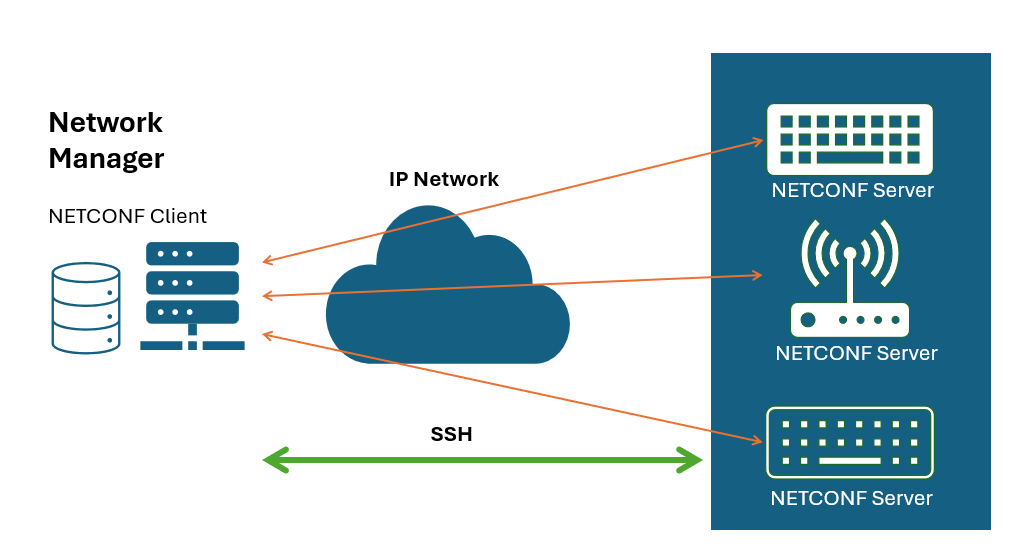
NETCONF Protocol Architecture - Client-Server Model
The NETCONF protocol architecture follows a client-server model where the NETCONF client initiates requests to the server (network device) to retrieve or modify configuration data. The NETCONF server responds to these requests with the required data or status information.
NETCONF client is typically part of a Network manager, that initiates requests to retrieve or modify the configuration and state data on network devices. The main functions of a NETCONF client include sending RPC requests to the NETCONF server (running on devices), receiving RPC replies from the NETCONF server, monitoring the devices for device health any unusual behavior.
NETCONF Server is part of a network devices such as a router, switch, firewall, or any other networked equipment. NETCONF server responds to the client’s requests, performing the required operations and returning the results. The main functions of a NETCONF server include processing the RPC requests from the NETCONF clients, configuration management on the devices, reporting of state, status and statistics, managing the datastores and sending notifications to the NETCONF clients.
As organizations increasingly demand real-time insights, ultra-low latency, and resilient distributed systems, Edge Computing is becoming mission-critical. At the same time, technologies like NETCONF are being integrated into Edge environments as a standard management and control layer.
To help professionals move confidently from concepts to execution, our course “Edge Computing Essentials: Concepts to Real-World Use Cases” provides a structured, hands-on learning path covering core principles, architecture, platforms, and enabling technologies—directly mapped to real-world industrial use cases.
If you’re looking to build in-demand skills and accelerate your career in Edge Computing, this is the right place to start.
Key Layers in NETCONF Protocol Architecture
The NETCONF protocol architecture is structured into several layers, each fulfilling specific roles and responsibilities in facilitating the configuration and management of network devices.
Here are the key layers in the NETCONF protocol architecture:
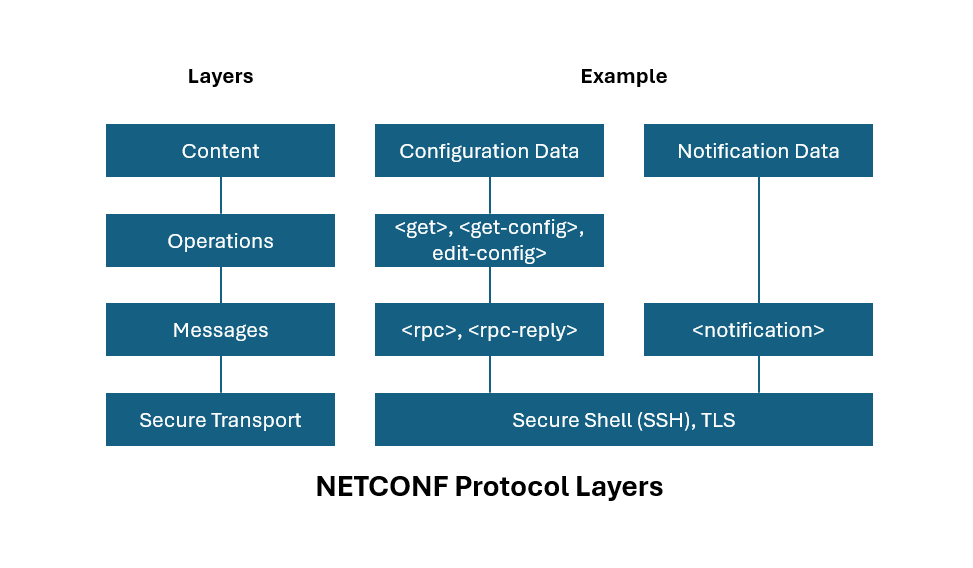
- Content Layer: Contains the actual configuration and state data encoded in XML.
- Operations Layer: Specifies the various operations that can be performed, such as <get-config>, <edit-config>, <copy-config>, and <delete-config>.
- Messages Layer: Defines the structure of messages exchanged between the client and server using XML.
- Transport Layer: Ensures secure communication between the client and server. Commonly used protocols include SSH and TLS.
NETCONF Sessions and Establishment
A NETCONF session is a secure communication channel established between a NETCONF client and a NETCONF server, allowing for the exchange of configuration and state data, execution of operations, and receiving notifications.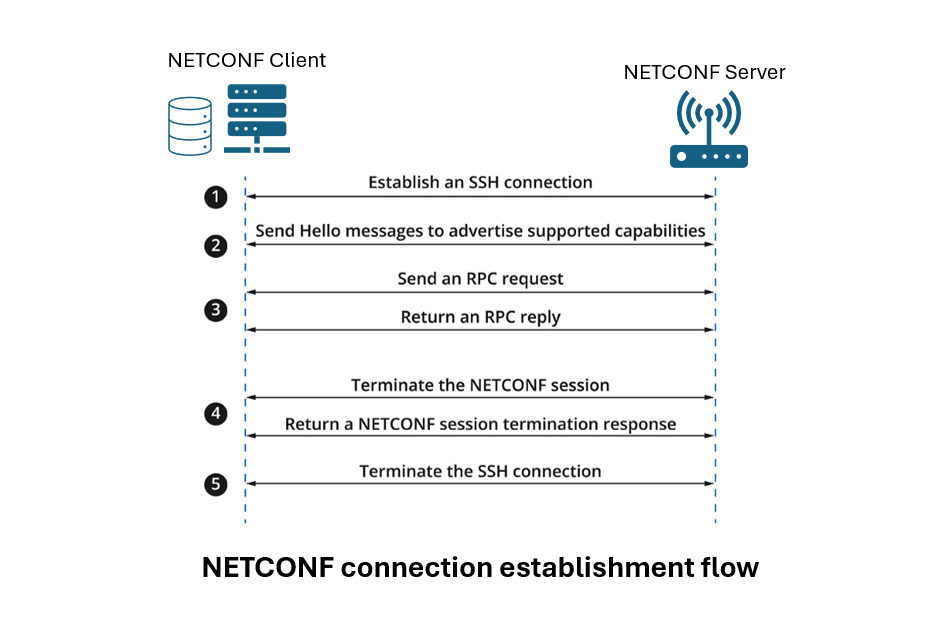
The process of establishing a NETCONF session involves several steps:
- Transport Layer Establishment: The client and server establish a secure communication channel using a protocol such as SSH.
- Session Initiation: The client initiates a NETCONF session by sending a hello message, indicating its capabilities.
- Capabilities Exchange: The server responds with its own hello message, listing its capabilities. This exchange allows both parties to understand what features and operations are supported.
- Operational Phase: Once the session is established, the client can send various NETCONF operations, such as retrieving configurations (get-config), editing configurations (edit-config), and more.
NETCONF Protocol Operations
NETCONF protocol operations are commands used to manage the configuration and state of network devices. These NETCONF protocol operations allow clients to perform various actions, such as retrieving configuration data, modifying configurations, and managing sessions. The operations are structured in XML and executed over a secure communication channel between the client and server.
Here are the key NETCONF protocol operations:
- <get-config>: Retrieves configuration data from a specified datastore (e.g., running, candidate, startup). It allows the client to fetch the current or intended configuration of the network device.
- <edit-config>: Modifies the configuration data in a specified datastore. It supports inserting, deleting, and merging configuration data, enabling detailed and flexible configuration changes.
- <copy-config>: Copies configuration data from one datastore to another. This operation is useful for tasks like backup, restore, and cloning configurations between datastores.
- <delete-config>: Deletes configuration data from a specified datastore. It is commonly used to clear the startup or candidate datastore, effectively resetting configurations.
- <lock>: Locks a datastore to prevent other clients from making changes. This ensures exclusive access to a datastore for critical operations, avoiding conflicts and ensuring consistency.
- <unlock>: Unlocks a previously locked datastore, allowing other clients to make changes again. It is used to release exclusive control after critical operations are completed.
- <commit>: Applies changes from the candidate datastore to the running datastore, making them active. This operation finalizes configuration changes and implements them on the device.
- <discard-changes>: Discards uncommitted changes in the candidate datastore, reverting it to its previous state. It is used to cancel changes that are not yet applied to the running configuration.
- <validate>: Validates the contents of a specified datastore without applying changes. This operation ensures that the configuration is correct and will not cause issues if applied.
- <get>: Retrieves running configuration and state information, including operational status and statistics. It provides a comprehensive view of the device's current state.
As organizations increasingly demand real-time insights, ultra-low latency, and resilient distributed systems, Edge Computing is becoming mission-critical. At the same time, technologies like NETCONF are being integrated into Edge environments as a standard management and control layer.
To help professionals move confidently from concepts to execution, our course “Edge Computing Essentials: Concepts to Real-World Use Cases” provides a structured, hands-on learning path covering core principles, architecture, platforms, and enabling technologies—directly mapped to real-world industrial use cases.
If you’re looking to build in-demand skills and accelerate your career in Edge Computing, this is the right place to start.
NETCONF Event Notifications
NETCONF event notifications allow a NETCONF server to asynchronously inform clients about significant events occurring on the network device. These NETCONF event notifications provide real-time updates about changes in device state, configuration, or operational status.
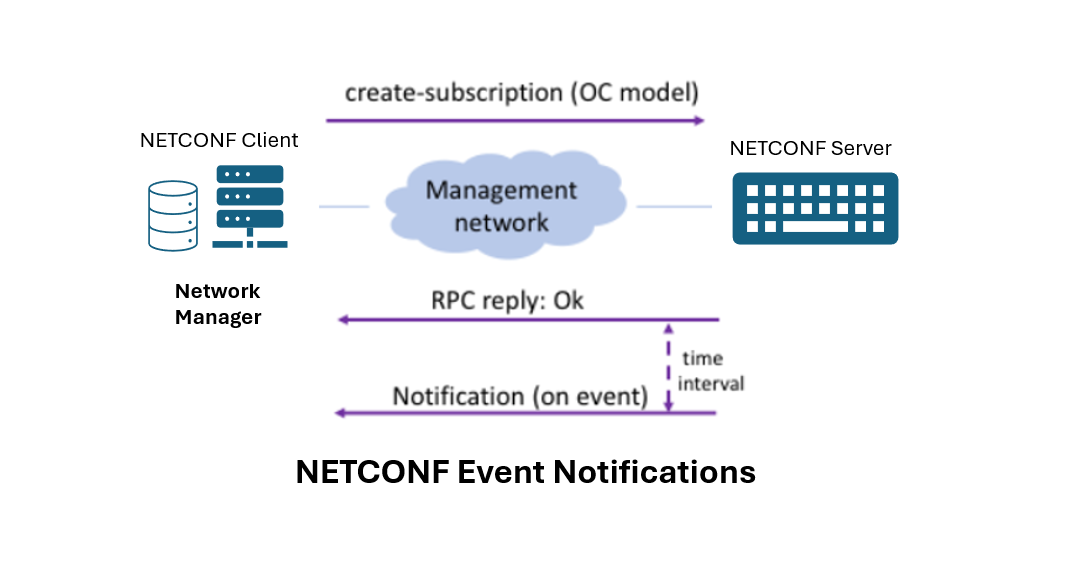
- NETCONF Event Notifications enable real-time updates without continuous polling, enhancing network monitoring efficiency.
- Clients can define and subscribe to specific event types, tailoring notifications to their monitoring needs.
- Subscriptions allow clients to specify filtering criteria and subscription duration, ensuring relevant updates are received.
- Notifications are structured in XML format, based on corresponding YANG models, ensuring interoperability.
- Secure delivery of notifications over the established NETCONF session ensures confidentiality and reliability.
- Subscriptions have defined lifespans, automatically expiring unless renewed by clients, optimizing resource utilization.
NETCONF Protocol Datastores
NETCONF defines majorly three datastores to manage the configuration data of network devices. Each datastore serves a different purpose and helps in organizing and handling the configurations effectively.
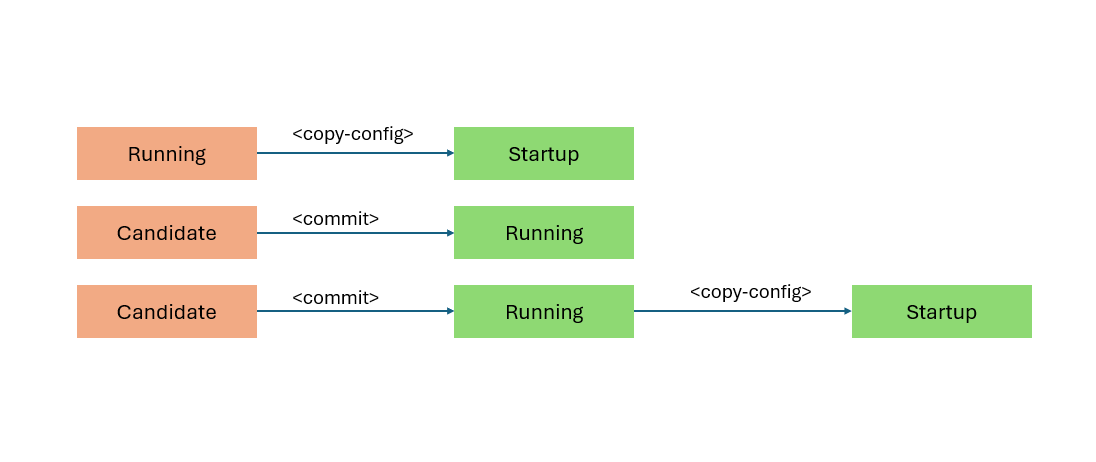
Here are the key NETCONF protocol datastores:
- Running Datastore: This is the active configuration datastore that the network device is currently using. All the operational settings and parameters are applied from this datastore. Changes made here are immediately active.
- Candidate Datastore: This is a writable configuration datastore that allows changes to be made without affecting the running configuration immediately. Administrators can prepare and validate configuration changes in the candidate datastore before committing them to the running datastore.
-
Startup Datastore: This datastore contains the configuration that the device uses when it boots up.
It is used to ensure that the device starts with a known good configuration.
NETCONF Capabilities and capabilities exchange
NETCONF Capabilities refer to the set of features and functions that a NETCONF server (typically a network device) supports, such as specific operations, datastores, and protocol extensions. These NETCONF capabilities are advertised in a standardized format when a NETCONF session is initiated.
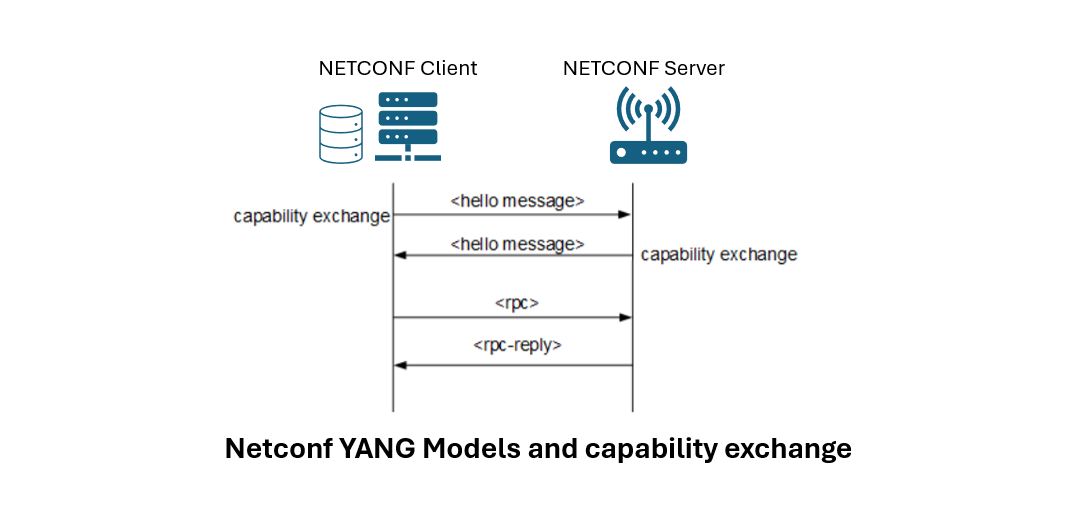
NETCONF Capabilities Exchange is the process during which both the client and server share their respective capabilities at the start of a session, allowing each to understand the supported features and operations of the other. This exchange ensures that both parties are aware of what functionalities can be used, facilitating interoperability and effective management of the network device.
YANG Models in NETCONF Protocol
YANG (Yet Another Next Generation) is a data modeling language used in the NETCONF protocol to model configuration and state data of network devices. YANG Models provides a standardized way to define the structure, format, and constraints of the data exchanged between NETCONF clients and servers.
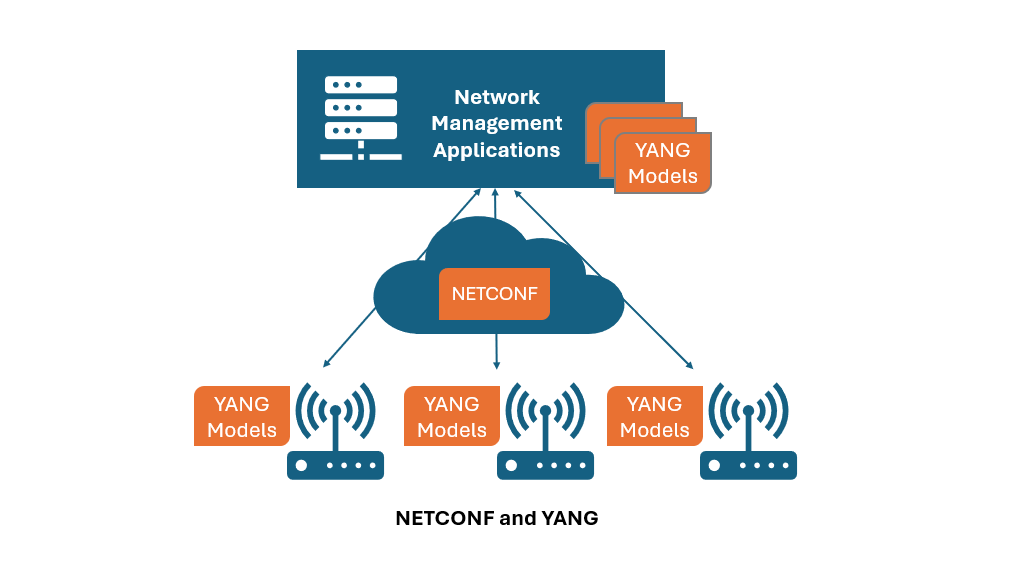
Key Features of YANG Models
- Data Hierarchy: Represents data in a hierarchical tree structure, simplifying organization and navigation.
- Modules and Submodules: Organized into modules with optional submodules for efficient management of complex data.
- Data Types and Constraints: Supports various data types and allows defining constraints to ensure data validity.
- RPCs and Notifications: Defines Remote Procedure Calls (RPCs) and notifications for dynamic client-server interactions.
- Extensibility and Reusability: Designed to be extensible with reusable groupings and typedefs for consistent definitions.
Example of a Simple YANG Model
module example-interfaces {
namespace "urn:example:interfaces";
prefix "if";
import ietf-yang-types {
prefix yang;
}
organization "Example Organization";
contact "example@example.com";
description "This module defines a simple interface model.";
container interfaces {
list interface {
key "name";
leaf name {
type string;
description "Name of the interface.";
}
leaf enabled {
type boolean;
default "true";
description "Whether the interface is enabled.";
}
leaf mtu {
type uint16 {
range "576..9000";
}
description "Maximum Transmission Unit size.";
}
}
}
}
YANG models NETCONF protocol play a crucial role, providing a standardized and extensible framework for defining and managing network configurations and state data.
Summary
NETCONF represents a significant advancement in network management protocols, offering standardized configuration management, transaction support, and enhanced security. By addressing the limitations of traditional methods like CLI and SNMP, NETCONF provides a more reliable and efficient solution for modern network environments.
- NETCONF is a standardized network management protocol defined by the IETF.
- It provides mechanisms for configuration management, monitoring, and remote procedure execution.
- NETCONF uses XML-based data encoding for structured communication between clients and servers.
- The protocol operates over secure transport protocols like SSH, TLS, and BEEP, ensuring data confidentiality and integrity.
- NETCONF supports transactional operations, allowing configuration changes to be applied atomically for consistency.
In the next part of our series, we will delve deeper into the NETCONF protocol implementation.
As organizations increasingly demand real-time insights, ultra-low latency, and resilient distributed systems, Edge Computing is becoming mission-critical. At the same time, technologies like NETCONF are being integrated into Edge environments as a standard management and control layer.
To help professionals move confidently from concepts to execution, our course “Edge Computing Essentials: Concepts to Real-World Use Cases” provides a structured, hands-on learning path covering core principles, architecture, platforms, and enabling technologies—directly mapped to real-world industrial use cases.
If you’re looking to build in-demand skills and accelerate your career in Edge Computing, this is the right place to start.